Running CI Scripts on Untrusted Forks
Untrusted forks could contain malicious code to mine cryptocurrency, steal secrets, or otherwise harm the CI server.
For PRs from untrusted forks, to run the CI scripts, we need to:
- Review the code to ensure that it is safe to run on the CI server.
- If the code is safe, run the
ci:trustscript to push the commits to a branch on the main repository, where the CI scripts can be run. - Once the tests have run, the status of the PR will be updated automatically (because the commits are the same).
How to run the CI scripts on untrusted forks:
- Copy the name of the branch from the PR.
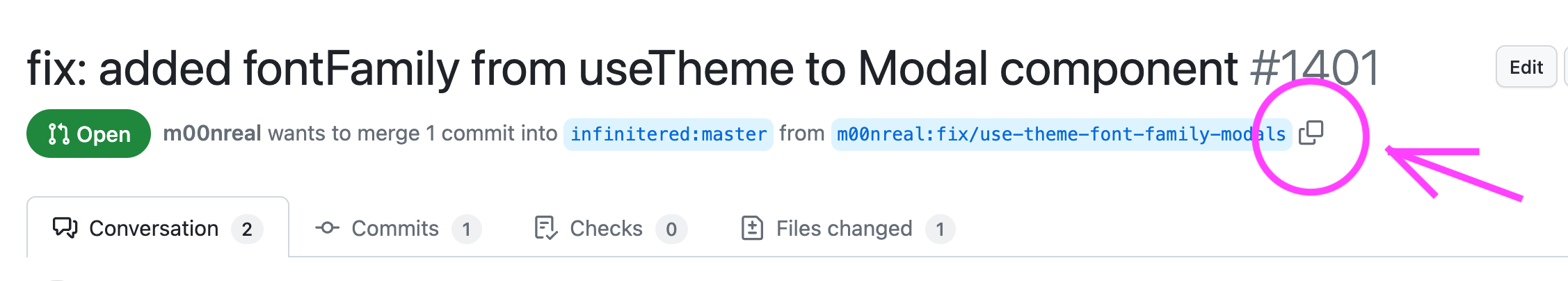
- From your local clone of the main repository, run the
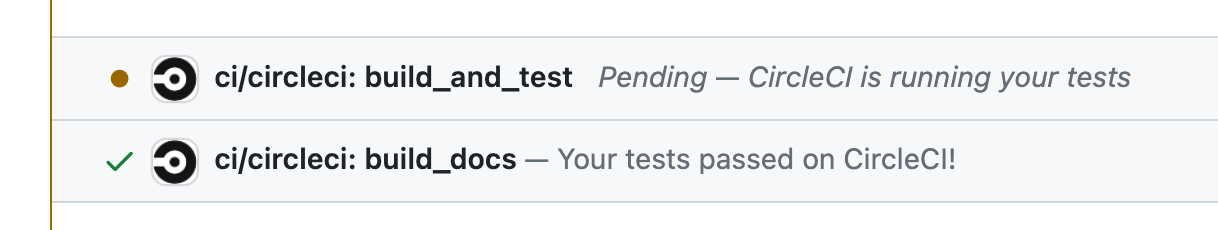
ci:trustscript.yarn ci:trust <branch-name> - The branch will be pushed and the tests will run
What does ci:trust do?
The ci:trust script does the following:
- Adds and fetches the untrusted fork as a temporary remote in your local repository.
- Pushes the specific branch from the untrusted fork to a designated temporary branch in your original repository.
- Pushing to a local branch triggers the continuous integration (CI) tests on the commits of the branch.
- Because the commits are the same, the status of the PR will be updated automatically.
Notes
- The ci:trust script will only work if you have write access to the main repository. This prevents malicious users from running the script on the main repository.
- The ci:trust script pushes the commits to a branch called
temp-ci-trusted-fork.
warning
The temp-ci-trusted-fork branch will be deleted and recreated if it already exists. This allows the script to
clean up its own temporary branches.